Clavister W30 reverse engineering
I disassembled a so called “next-generation firewall” which has been produced by the Swedish company Clavister. It’s basically an x86 machine with quite some Ethernet ports. They seem quite expensive, even a discounted version of the W30 costs an equivalent of 1500 US dollars on some webshop. I got one for free ¯\_(ツ)_/¯
Hardware
The W30 model is based on an Intel Atom C2558, which was labled “SR1CZ” on the die. The main storage is a 1GiB “Industrial” CompactFlash card. The power supply contains an unpopulated SATA cable. There is an 2GiB DDR3-1333 DIMM. The 8 Gbit Ethernet ports on the right side are connected through PCIe, but it uses some weird card to make the right angle. There also is a Nuoveton NCT6776F chip on the motherboard, which is the Super I/O. The serial is using RJ45, which can be connected to a normal machine using a USB TTY cable. The same concept is used on Cisco devices.
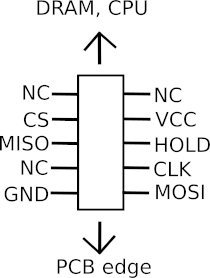
On the other side of the PCB, there is a Winbond 25064FVSIG SPI flash chip available with some very convienient “SPIROM1” labeled pin header on the upper side of the mainboard! Although the pinout is unknown, so I still had to check it with a multimeter.
The pinout is as follows:
Firmware
After booting the device, there is a shell over serial. It runs on some proprietary operating system called Clavister cOS Core. From the marketing materials it appears to be some operating system developed by themselves.
Device:/> about
Clavister cOS Core 11.04.00.48-29833
Copyright Clavister 1996-2016. All rights reserved
QuickSec 3.2.0
Build : Jun 30 2016
QuickSec appears to be some IPSec implementation from the company called SafeNet, which is likely licensed and integrated into the device by Clavister. SafeNet has been aquired by Thales Group since then.
The CF card inside the system is a DOS/MBR filesystem which contains some firmware spread out over various files. Most of the webinterface stuff is located inside WEBUI.RC, which starts with a Portable Executable header.
The file called “fwcore.cfx” sounds the most interesting, due to its name and size (6.6M)
running binwalk -E on it, shows a high entropy, which suggests that is is either compressed or encrypted. Binwalk suggests that it uses bzip2, but bunzip2 is not able to unpack it.
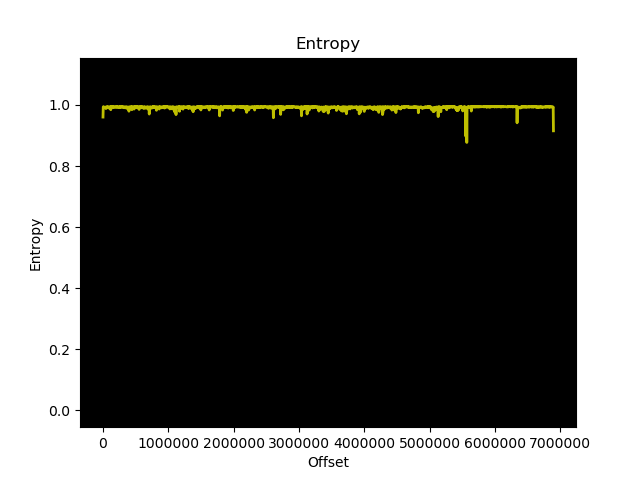
bzip2 is a format that uses several different transformations and encodings together to compress a single file. The files were combined together using tar in the “FACTORY.DEF” file. The utility bzip2recover can look for blocks inside the bzip2’ed file and extract those in one file per block. After running this utility on the fwcore.cfx, it creates 138 different files. Those can be combined into a single file again using cat. Running binwalk again on this file reveals quite some interesting strings. The operating seems to be based on the open source (GPL with linking exception) eCos RTOS. The fwcore.cfx does import the fwloader.cfx as an external library.
strings from the BOOTMENU.CFX don’t give me any Google hits, so I suppose it is some kind of internally developed bootloader.
User_SecurityEnabled()
I have dumped the firmware on the SPI chip using a Raspberry Pi and the flashrom utility. Running Binwalk on the firmware indicated that it uses an UEFI firmware from American Megatrends. It can be inspected using UEFITool. I have currently no idea how this devices chooses the right file on the storage, because they don’t seem to be EFI files.
It’d be a very interesting device for OpenWrt, considering the quite good specifications compared to regular consumer routers.
Work in progress…